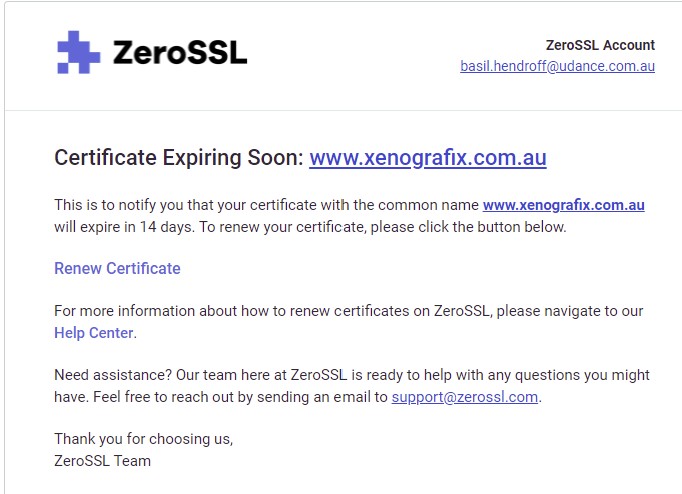
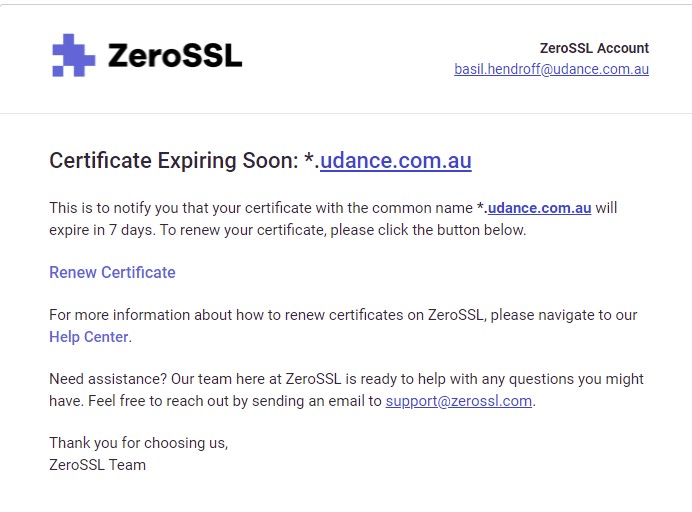
That’s the strange part. There’s nothing except for internal CA renewals to support mTLS. For example:
root@caddy:/var/log/caddy # tail --lines=21 caddy.11
{"level":"info","ts":"2021-08-12T12:02:59.827+0800","logger":"tls.cache.maintenance","msg":"certificate expires soon; queuing for renewal","identifiers":["acme.lan"],"remaining":14399.172172962}
{"level":"info","ts":"2021-08-12T12:02:59.841+0800","logger":"tls.cache.maintenance","msg":"attempting certificate renewal","identifiers":["acme.lan"],"remaining":14399.158377993}
{"level":"info","ts":"2021-08-12T12:02:59.881+0800","logger":"tls.renew","msg":"acquiring lock","identifier":"acme.lan"}
{"level":"info","ts":"2021-08-12T12:02:59.929+0800","logger":"tls.renew","msg":"lock acquired","identifier":"acme.lan"}
{"level":"info","ts":"2021-08-12T12:02:59.930+0800","logger":"tls.renew","msg":"renewing certificate","identifier":"acme.lan","remaining":14399.069867861}
{"level":"info","ts":"2021-08-12T12:02:59.931+0800","logger":"tls.renew","msg":"certificate renewed successfully","identifier":"acme.lan"}
{"level":"info","ts":"2021-08-12T12:02:59.931+0800","logger":"tls.renew","msg":"releasing lock","identifier":"acme.lan"}
{"level":"info","ts":"2021-08-12T12:02:59.932+0800","logger":"tls","msg":"reloading managed certificate","identifiers":["acme.lan"]}
{"level":"warn","ts":"2021-08-12T12:02:59.948+0800","logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [acme.lan]: no OCSP server specified in certificate"}
{"level":"info","ts":"2021-08-12T12:02:59.948+0800","logger":"tls.cache","msg":"replaced certificate in cache","identifiers":["acme.lan"],"new_expiration":"2021-08-12T16:02:59.000Z"}
2021/08/12 12:39:52 {"id":"s4qx7CCHVoRlWgpAOunvpS0iY4nKllDi","status":"pending","expires":"2021-08-13T04:39:52Z","identifiers":[{"type":"dns","value":"file.lan"}],"notBefore":"2021-08-12T04:38:52Z","notAfter":"2021-08-12T16:39:52Z","authorizations":["https://acme.lan/acme/local/authz/OPqVVBTy8ZNzCp9aLwgCIyjF34AHQNK2"],"finalize":"https://acme.lan/acme/local/order/s4qx7CCHVoRlWgpAOunvpS0iY4nKllDi/finalize"}
2021/08/12 12:39:52 {"identifier":{"type":"dns","value":"file.lan"},"status":"pending","challenges":[{"type":"dns-01","status":"pending","token":"4idn4kZOpIPwndABM9VWM0yErs3Bu79S","url":"https://acme.lan/acme/local/challenge/OPqVVBTy8ZNzCp9aLwgCIyjF34AHQNK2/EJtT0gA5mqsNhmi91eLx5c3k9SDwh1iR"},{"type":"http-01","status":"pending","token":"4idn4kZOpIPwndABM9VWM0yErs3Bu79S","url":"https://acme.lan/acme/local/challenge/OPqVVBTy8ZNzCp9aLwgCIyjF34AHQNK2/ZuOTHwUl1J2njQIm3VsrdURxX1z3gW1k"},{"type":"tls-alpn-01","status":"pending","token":"4idn4kZOpIPwndABM9VWM0yErs3Bu79S","url":"https://acme.lan/acme/local/challenge/OPqVVBTy8ZNzCp9aLwgCIyjF34AHQNK2/YPMqCNmy0BV4tpCPcAjjMBTlYns0DJaG"}],"wildcard":false,"expires":"2021-08-13T04:39:52Z"}
2021/08/12 12:39:52 {"type":"tls-alpn-01","status":"valid","token":"4idn4kZOpIPwndABM9VWM0yErs3Bu79S","validated":"2021-08-12T04:39:52Z","url":"https://acme.lan/acme/local/challenge/OPqVVBTy8ZNzCp9aLwgCIyjF34AHQNK2/YPMqCNmy0BV4tpCPcAjjMBTlYns0DJaG"}
2021/08/12 12:39:52 {"identifier":{"type":"dns","value":"file.lan"},"status":"valid","challenges":[{"type":"dns-01","status":"pending","token":"4idn4kZOpIPwndABM9VWM0yErs3Bu79S","url":"https://acme.lan/acme/local/challenge/OPqVVBTy8ZNzCp9aLwgCIyjF34AHQNK2/EJtT0gA5mqsNhmi91eLx5c3k9SDwh1iR"},{"type":"http-01","status":"pending","token":"4idn4kZOpIPwndABM9VWM0yErs3Bu79S","url":"https://acme.lan/acme/local/challenge/OPqVVBTy8ZNzCp9aLwgCIyjF34AHQNK2/ZuOTHwUl1J2njQIm3VsrdURxX1z3gW1k"},{"type":"tls-alpn-01","status":"valid","token":"4idn4kZOpIPwndABM9VWM0yErs3Bu79S","validated":"2021-08-12T04:39:52Z","url":"https://acme.lan/acme/local/challenge/OPqVVBTy8ZNzCp9aLwgCIyjF34AHQNK2/YPMqCNmy0BV4tpCPcAjjMBTlYns0DJaG"}],"wildcard":false,"expires":"2021-08-13T04:39:52Z"}
2021/08/12 12:39:52 {"id":"s4qx7CCHVoRlWgpAOunvpS0iY4nKllDi","status":"valid","expires":"2021-08-13T04:39:52Z","identifiers":[{"type":"dns","value":"file.lan"}],"notBefore":"2021-08-12T04:38:52Z","notAfter":"2021-08-12T16:39:52Z","authorizations":["https://acme.lan/acme/local/authz/OPqVVBTy8ZNzCp9aLwgCIyjF34AHQNK2"],"finalize":"https://acme.lan/acme/local/order/s4qx7CCHVoRlWgpAOunvpS0iY4nKllDi/finalize","certificate":"https://acme.lan/acme/local/certificate/u0lG1EQ4XXrdu6iC5YvQ0Vv9BSdsd5ch"}
2021/08/12 13:25:43 {"newNonce":"https://acme.lan/acme/local/new-nonce","newAccount":"https://acme.lan/acme/local/new-account","newOrder":"https://acme.lan/acme/local/new-order","revokeCert":"https://acme.lan/acme/local/revoke-cert","keyChange":"https://acme.lan/acme/local/key-change"}
2021/08/12 13:25:44 {"id":"NQB8V3xWVWSp3jo9ZcocacCGbciH0yIq","status":"pending","expires":"2021-08-13T05:25:43Z","identifiers":[{"type":"dns","value":"mockup.lan"}],"notBefore":"2021-08-12T05:24:43Z","notAfter":"2021-08-12T17:25:43Z","authorizations":["https://acme.lan/acme/local/authz/mepwNqeXVANCBw4TzVMlmcor8LXKQJTw"],"finalize":"https://acme.lan/acme/local/order/NQB8V3xWVWSp3jo9ZcocacCGbciH0yIq/finalize"}
2021/08/12 13:25:44 {"identifier":{"type":"dns","value":"mockup.lan"},"status":"pending","challenges":[{"type":"dns-01","status":"pending","token":"yH1ZlT9WLasw0xbgOemEufOskyv1QfKU","url":"https://acme.lan/acme/local/challenge/mepwNqeXVANCBw4TzVMlmcor8LXKQJTw/4vyXio4bQO6gqIhOUkOlBG5b13asH1Uq"},{"type":"http-01","status":"pending","token":"yH1ZlT9WLasw0xbgOemEufOskyv1QfKU","url":"https://acme.lan/acme/local/challenge/mepwNqeXVANCBw4TzVMlmcor8LXKQJTw/KGeG0TAqdyr2RNgRhc8wxCX8h50tcCAi"},{"type":"tls-alpn-01","status":"pending","token":"yH1ZlT9WLasw0xbgOemEufOskyv1QfKU","url":"https://acme.lan/acme/local/challenge/mepwNqeXVANCBw4TzVMlmcor8LXKQJTw/EdhrPFNVB0GDAfD1tIRr4SQlbb9WJ2Ws"}],"wildcard":false,"expires":"2021-08-13T05:25:43Z"}
2021/08/12 13:25:44 {"type":"http-01","status":"valid","token":"yH1ZlT9WLasw0xbgOemEufOskyv1QfKU","validated":"2021-08-12T05:25:44Z","url":"https://acme.lan/acme/local/challenge/mepwNqeXVANCBw4TzVMlmcor8LXKQJTw/KGeG0TAqdyr2RNgRhc8wxCX8h50tcCAi"}
2021/08/12 13:25:44 {"identifier":{"type":"dns","value":"mockup.lan"},"status":"valid","challenges":[{"type":"dns-01","status":"pending","token":"yH1ZlT9WLasw0xbgOemEufOskyv1QfKU","url":"https://acme.lan/acme/local/challenge/mepwNqeXVANCBw4TzVMlmcor8LXKQJTw/4vyXio4bQO6gqIhOUkOlBG5b13asH1Uq"},{"type":"http-01","status":"valid","token":"yH1ZlT9WLasw0xbgOemEufOskyv1QfKU","validated":"2021-08-12T05:25:44Z","url":"https://acme.lan/acme/local/challenge/mepwNqeXVANCBw4TzVMlmcor8LXKQJTw/KGeG0TAqdyr2RNgRhc8wxCX8h50tcCAi"},{"type":"tls-alpn-01","status":"pending","token":"yH1ZlT9WLasw0xbgOemEufOskyv1QfKU","url":"https://acme.lan/acme/local/challenge/mepwNqeXVANCBw4TzVMlmcor8LXKQJTw/EdhrPFNVB0GDAfD1tIRr4SQlbb9WJ2Ws"}],"wildcard":false,"expires":"2021-08-13T05:25:43Z"}
2021/08/12 13:25:44 {"id":"NQB8V3xWVWSp3jo9ZcocacCGbciH0yIq","status":"valid","expires":"2021-08-13T05:25:43Z","identifiers":[{"type":"dns","value":"mockup.lan"}],"notBefore":"2021-08-12T05:24:43Z","notAfter":"2021-08-12T17:25:43Z","authorizations":["https://acme.lan/acme/local/authz/mepwNqeXVANCBw4TzVMlmcor8LXKQJTw"],"finalize":"https://acme.lan/acme/local/order/NQB8V3xWVWSp3jo9ZcocacCGbciH0yIq/finalize","certificate":"https://acme.lan/acme/local/certificate/03YthqFkgvuQOhkfykBMslaQ4iEotgFK"}
When I search for a particular domain, I see lines like the following where Caddy has been restarted and that’s about it:
{"level":"info","ts":"2021-08-11T02:53:05.919+0800","logger":"http","msg":"enabling automatic TLS certificate management","domains":["caffigoalkeeping.com.au","udance.com.au","www.caffigoalkeeping.com.au","www.caffigoalkeeping.com","readymcgetty.com.au","acme.lan","caffigoalkeeping.com","*.udance.com.au","www.readymcgetty.com.au","www.udance.com.au","www.xenografix.com.au","xenografix.com.au"]}
Here’s an extract of the log when I last had debug enabled:
{"level":"info","ts":"2021-07-10T13:35:34.767+0800","logger":"http","msg":"enabling automatic TLS certificate management","domains":["www.caffigoalkeeping.com.au","www.xenografix.com.au","xenografix.com.au","www.caffigoalkeeping.com","*.udance.com.au","caffigoalkeeping.com.au","www.readymcgetty.com.au","readymcgetty.com.au","www.udance.com.au","caffigoalkeeping.com","udance.com.au","acme.lan"]}
{"level":"debug","ts":"2021-07-10T13:35:34.768+0800","logger":"tls","msg":"loading managed certificate","domain":"www.caffigoalkeeping.com.au","expiration":"2021-08-30T18:17:55.000Z","issuer_key":"acme-v02.api.letsencrypt.org-directory","storage":"FileStorage:/var/db/caddy/data/caddy"}
{"level":"debug","ts":"2021-07-10T13:35:34.768+0800","logger":"tls","msg":"loading managed certificate","domain":"www.xenografix.com.au","expiration":"2021-08-30T18:17:57.000Z","issuer_key":"acme-v02.api.letsencrypt.org-directory","storage":"FileStorage:/var/db/caddy/data/caddy"}
{"level":"debug","ts":"2021-07-10T13:35:34.769+0800","logger":"tls","msg":"loading managed certificate","domain":"xenografix.com.au","expiration":"2021-08-30T23:59:59.000Z","issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/db/caddy/data/caddy"}
{"level":"debug","ts":"2021-07-10T13:35:34.770+0800","logger":"tls","msg":"loading managed certificate","domain":"www.caffigoalkeeping.com","expiration":"2021-08-30T18:24:18.000Z","issuer_key":"acme-v02.api.letsencrypt.org-directory","storage":"FileStorage:/var/db/caddy/data/caddy"}
{"level":"debug","ts":"2021-07-10T13:35:34.771+0800","logger":"tls","msg":"loading managed certificate","domain":"*.udance.com.au","expiration":"2021-08-30T19:06:12.000Z","issuer_key":"acme-v02.api.letsencrypt.org-directory","storage":"FileStorage:/var/db/caddy/data/caddy"}
{"level":"debug","ts":"2021-07-10T13:35:34.773+0800","logger":"tls","msg":"loading managed certificate","domain":"caffigoalkeeping.com.au","expiration":"2021-08-30T23:59:59.000Z","issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/db/caddy/data/caddy"}
{"level":"debug","ts":"2021-07-10T13:35:34.774+0800","logger":"tls","msg":"loading managed certificate","domain":"www.readymcgetty.com.au","expiration":"2021-08-30T23:59:59.000Z","issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/db/caddy/data/caddy"}
{"level":"debug","ts":"2021-07-10T13:35:34.775+0800","logger":"tls","msg":"loading managed certificate","domain":"readymcgetty.com.au","expiration":"2021-08-30T18:17:57.000Z","issuer_key":"acme-v02.api.letsencrypt.org-directory","storage":"FileStorage:/var/db/caddy/data/caddy"}
{"level":"debug","ts":"2021-07-10T13:35:34.776+0800","logger":"tls","msg":"loading managed certificate","domain":"www.udance.com.au","expiration":"2021-08-30T18:18:02.000Z","issuer_key":"acme-v02.api.letsencrypt.org-directory","storage":"FileStorage:/var/db/caddy/data/caddy"}
{"level":"debug","ts":"2021-07-10T13:35:34.778+0800","logger":"tls","msg":"loading managed certificate","domain":"caffigoalkeeping.com","expiration":"2021-08-30T23:59:59.000Z","issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/db/caddy/data/caddy"}
{"level":"debug","ts":"2021-07-10T13:35:34.779+0800","logger":"tls","msg":"loading managed certificate","domain":"udance.com.au","expiration":"2021-08-30T18:17:51.000Z","issuer_key":"acme-v02.api.letsencrypt.org-directory","storage":"FileStorage:/var/db/caddy/data/caddy"}
It’s all rather confusing. For instance, this last extract suggests that the wildcard certificate *.udance.com.au was issued by Let’s Encrypt. Could it be that things got messed up while I was working on mTLS? I do recall deleting the Caddy data storage location on several occasions? If so, is there a way to ‘reset’ and have my certs renewed and issued by the default CA?