1. Caddy version (caddy version):
v2.4.3 h1:Y1FaV2N4WO3rBqxSYA8UZsZTQdN+PwcoOcAiZTM8C0I=
2. How I run Caddy:
haproxy on 80/443 which is handed off to caddy 8080/8443
a. System environment:
Ubuntu 20.04
b. Command:
Systemd?
systemctl start/stop/etc caddy
c. Service/unit/compose file:
[Unit]
Description=Caddy
Documentation=https://caddyserver.com/docs/
After=network.target network-online.target
Requires=network-online.target
[Service]
Type=notify
User=exec
Group=exec
ExecStart=/usr/bin/caddy run --environ --config /etc/caddy/Caddyfile
ExecReload=/usr/bin/caddy reload --config /etc/caddy/Caddyfile
TimeoutStopSec=5s
LimitNOFILE=1048576
LimitNPROC=512
PrivateTmp=true
ProtectSystem=full
AmbientCapabilities=CAP_NET_BIND_SERVICE
[Install]
WantedBy=multi-user.target
d. My complete Caddyfile or JSON config:
{
http_port 8080
https_port 8443
}
x.y.z {
root * /server/web-server/public-html/x.y.z/
php_fastcgi unix//run/php/php7.4-fpm.sock
file_server
}
3. The problem I’m having:
Hi there.
I have a setup where haproxy (80/443) is in-front of caddy (127.0.0.1:8080/8443)
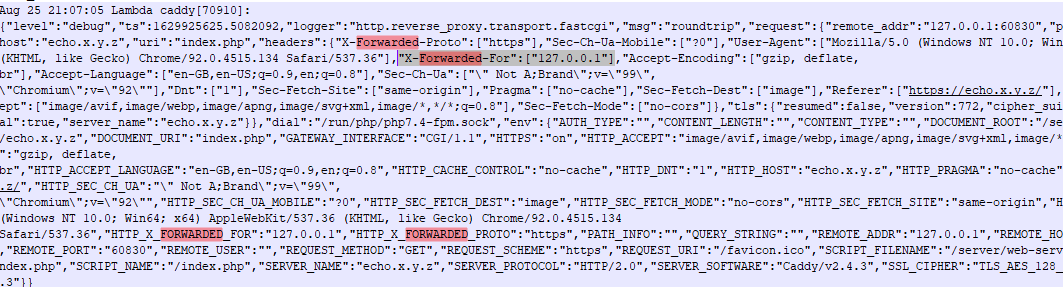
I am trying to make it so that caddy knows the ‘Real IP’ of the request, passed through haproxy, using the X-Forwarded-For header.
It seems that Caddy does not ‘pass through’ this header AND/OR discards this header AND/OR does something where, when I attempt to print $_SERVER['X-Forwarded-For'] with php-fpm, I get the wrong answer.
HTTP_X_FORWARDED_FOR=127.0.0.1
If I replace / hot-swap Caddy with Nginx, and print the same header, using the same copy of php-fpm wired up to Nginx, then the header is passed through correctly. (i.e. the ‘Real IP’ of that request, not the 127.0.0.1 ‘proxy_passed’ localhost address)
HTTP_X_FORWARDED_FOR=185.223.XXX.X
Here is my crude haproxy configuration
frontend frontend-http
bind *:80
mode http
default_backend backend-caddy-http
#option httpclose
option forwardfor
# reqidel ^X-Forwarded-For:.*
# http-request add-header X-Forwarded-For %[src]
frontend frontend-https
bind *:443
mode tcp
default_backend backend-caddy-https
#option httpclose
option forwardfor
# reqidel ^X-Forwarded-For:.*
# http-request add-header X-Forwarded-For %[src]
backend backend-caddy-http
mode http
server frontend-http 127.0.0.1:8080 # Caddy/Nginx HTTP on 8080
#option httpclose
option forwardfor
# reqidel ^X-Forwarded-For:.*
# http-request add-header X-Forwarded-For %[src]
backend backend-caddy-https
mode tcp
server frontend-https 127.0.0.1:8443 # Caddy/Nginx HTTPS on 8443
#option httpclose
option forwardfor
# reqidel ^X-Forwarded-For:.*
# http-request add-header X-Forwarded-For %[src]
Is this a bug? Any pointers, advise or links to documentation explaining what Caddy v2 is doing with with the request headers in-between the time Caddy receives the request from Haproxy, and the time it takes to print the header out to screen, would be greatly appreciated.
Also, setting the log level to DEBUG and looking at the Caddy logs, when doing a request, it doesn’t show the X-Forwarded headers in the request.headers section.
{
"level": "info",
"ts": 1629922024.871911,
"logger": "http.log.access.log0",
"msg": "handled request",
"request": {
"remote_addr": "127.0.0.1:60754",
"proto": "HTTP/2.0",
"method": "GET",
"host": "x.y.z",
"uri": "/",
"headers": {
"Cache-Control": ["max-age=0"],
"Accept": ["text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9"],
"Sec-Fetch-Site": ["none"],
"Sec-Fetch-Mode": ["navigate"],
"Sec-Fetch-User": ["?1"],
"Sec-Fetch-Dest": ["document"],
"Sec-Ch-Ua": ["\" Not A;Brand\";v=\"99\", \"Chromium\";v=\"92\""],
"Sec-Ch-Ua-Mobile": ["?0"],
"Dnt": ["1"],
"Upgrade-Insecure-Requests": ["1"],
"User-Agent": ["Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.134 Safari/537.36"],
"Accept-Encoding": ["gzip, deflate, br"],
"Accept-Language": ["en-GB,en-US;q=0.9,en;q=0.8"]
},
"tls": {
"resumed": true,
"version": 772,
"cipher_suite": 4865,
"proto": "h2",
"proto_mutual": true,
"server_name": "x.y.z"
}
},
"common_log": "127.0.0.1 - - [25/Aug/2021:20:07:04 +0000] \"GET / HTTP/2.0\" 200 1876",
"duration": 0.000758017,
"size": 1876,
"status": 200,
"resp_headers": {
"Server": ["Caddy"],
"Content-Type": ["text/html; charset=UTF-8"]
}
}{
"level": "info",
"ts": 1629922025.0205097,
"logger": "http.log.access.log0",
"msg": "handled request",
"request": {
"remote_addr": "127.0.0.1:60754",
"proto": "HTTP/2.0",
"method": "GET",
"host": "x.y.z",
"uri": "/favicon.ico",
"headers": {
"Pragma": ["no-cache"],
"Cache-Control": ["no-cache"],
"Sec-Ch-Ua": ["\" Not A;Brand\";v=\"99\", \"Chromium\";v=\"92\""],
"Dnt": ["1"],
"Sec-Ch-Ua-Mobile": ["?0"],
"Accept": ["image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8"],
"Sec-Fetch-Mode": ["no-cors"],
"Sec-Fetch-Dest": ["image"],
"Referer": ["https://x.y.z"],
"Accept-Language": ["en-GB,en-US;q=0.9,en;q=0.8"],
"User-Agent": ["Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.134 Safari/537.36"],
"Sec-Fetch-Site": ["same-origin"],
"Accept-Encoding": ["gzip, deflate, br"]
},
"tls": {
"resumed": true,
"version": 772,
"cipher_suite": 4865,
"proto": "h2",
"proto_mutual": true,
"server_name": "x.y.z"
}
},
"common_log": "127.0.0.1 - - [25/Aug/2021:20:07:05 +0000] \"GET /favicon.ico HTTP/2.0\" 200 1818",
"duration": 0.000800669,
"size": 1818,
"status": 200,
"resp_headers": {
"Server": ["Caddy"],
"Content-Type": ["text/html; charset=UTF-8"]
}
}
Thanks.