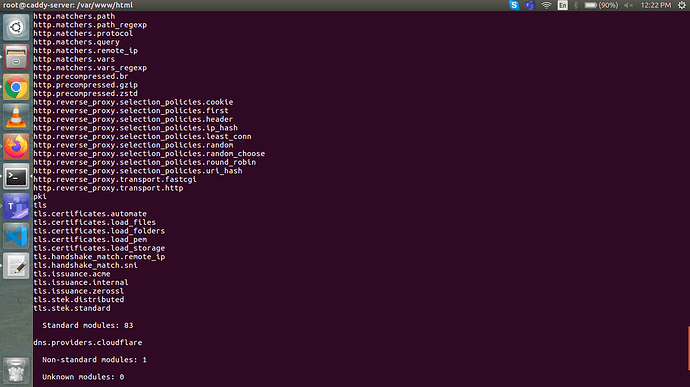
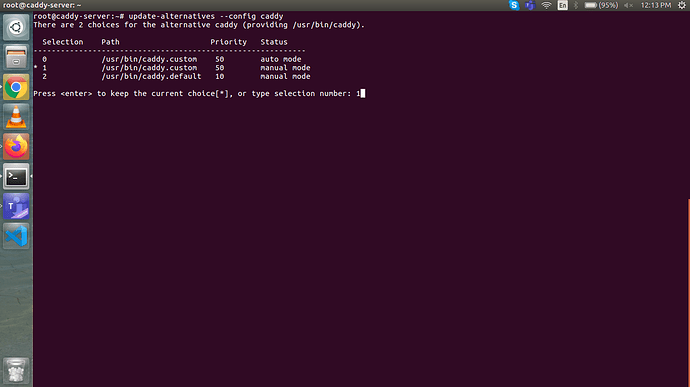
Hello Matt,
Thanks for your reply.
Sorry for not posting the full log.
Here is the full log -
2021/06/28 04:09:35.842 INFO admin admin endpoint started {"address": "tcp/localhost:2019", "enforce_origin": false, "origins": ["localhost:2019", "[::1]:2019", "127.0.0.1:2019"]}
2021/06/28 04:09:35.842 INFO serving initial configuration
2021/06/28 04:09:52.429 INFO admin.api received request {"method": "POST", "host": "localhost:2019", "uri": "/load", "remote_addr": "127.0.0.1:47684", "headers": {"Accept-Encoding":["gzip"],"Content-Length":["2333"],"Content-Type":["application/json"],"Origin":["localhost:2019"],"User-Agent":["Go-http-client/1.1"]}}
2021/06/28 04:09:52.430 INFO admin admin endpoint started {"address": "tcp/localhost:2019", "enforce_origin": false, "origins": ["localhost:2019", "[::1]:2019", "127.0.0.1:2019"]}
2021/06/28 04:09:52.431 INFO http server is listening only on the HTTPS port but has no TLS connection policies; adding one to enable TLS{"server_name": "example", "https_port": 443}
2021/06/28 04:09:52.431 INFO http enabling automatic HTTP->HTTPS redirects {"server_name": "example"}
2021/06/28 04:09:52.432 DEBUG http starting server loop {"address": "[::]:443", "http3": false, "tls": true}
2021/06/28 04:09:52.433 DEBUG http starting server loop {"address": "[::]:80", "http3": false, "tls": false}
2021/06/28 04:09:52.434 INFO http enabling automatic TLS certificate management {"domains": ["example.com", "*.example111.com"]}
2021/06/28 04:09:52.434 DEBUG tls loading managed certificate {"domain": "example.com", "expiration": "2021/08/02 07:57:55.000", "issuer_key": "acme-v02.api.letsencrypt.org-directory", "storage": "FileStorage:/root/.local/share/caddy"}
2021/06/28 04:09:52.444 INFO autosaved config {"file": "/root/.config/caddy/autosave.json"}
2021/06/28 04:09:52.444 INFO admin.api load complete
2021/06/28 04:09:52.433 INFO tls cleaned up storage units
2021/06/28 04:09:52.431 INFO tls.cache.maintenance started background certificate maintenance {"cache": "0xc00022a9a0"}
2021/06/28 04:09:52.451 INFO tls.obtain acquiring lock {"identifier": "*.example111.com"}
2021/06/28 04:09:52.452 INFO tls.obtain lock acquired {"identifier": "*.example111.com"}
2021/06/28 04:09:52.453 INFO tls.issuance.acme waiting on internal rate limiter {"identifiers": ["*.example111.com"]}
2021/06/28 04:09:52.453 INFO tls.issuance.acme done waiting on internal rate limiter {"identifiers": ["*.example111.com"]}
2021/06/28 04:09:52.932 INFO admin stopped previous server
2021/06/28 04:09:53.063 DEBUG tls.issuance.acme.acme_client http request {"method": "GET", "url": "https://acme-v02.api.letsencrypt.org/directory", "headers": {"User-Agent":["Caddy/2.3.0 CertMagic acmez (linux; amd64)"]}, "status_code": 200, "response_headers": {"Cache-Control":["public, max-age=0, no-cache"],"Content-Length":["658"],"Content-Type":["application/json"],"Date":["Mon, 28 Jun 2021 04:09:52 GMT"],"Server":["nginx"],"Strict-Transport-Security":["max-age=604800"],"X-Frame-Options":["DENY"]}}
2021/06/28 04:09:53.204 DEBUG tls.issuance.acme.acme_client http request {"method": "HEAD", "url": "https://acme-v02.api.letsencrypt.org/acme/new-nonce", "headers": {"User-Agent":["Caddy/2.3.0 CertMagic acmez (linux; amd64)"]}, "status_code": 200, "response_headers": {"Cache-Control":["public, max-age=0, no-cache"],"Date":["Mon, 28 Jun 2021 04:09:53 GMT"],"Link":["<https://acme-v02.api.letsencrypt.org/directory>;rel=\"index\""],"Replay-Nonce":["000417ZjLb770B8hBEZan73z82Fyfy6ACFHln4tUnoozd00"],"Server":["nginx"],"Strict-Transport-Security":["max-age=604800"],"X-Frame-Options":["DENY"]}}
2021/06/28 04:09:53.374 DEBUG tls.issuance.acme.acme_client http request {"method": "POST", "url": "https://acme-v02.api.letsencrypt.org/acme/new-order", "headers": {"Content-Type":["application/jose+json"],"User-Agent":["Caddy/2.3.0 CertMagic acmez (linux; amd64)"]}, "status_code": 201, "response_headers": {"Boulder-Requester":["118231829"],"Cache-Control":["public, max-age=0, no-cache"],"Content-Length":["336"],"Content-Type":["application/json"],"Date":["Mon, 28 Jun 2021 04:09:53 GMT"],"Link":["<https://acme-v02.api.letsencrypt.org/directory>;rel=\"index\""],"Location":["https://acme-v02.api.letsencrypt.org/acme/order/118231829/10697296104"],"Replay-Nonce":["0003-M4GitSQLt0OB9lLQQYOxri-_NdoMW4TtIO6wEY1OQo"],"Server":["nginx"],"Strict-Transport-Security":["max-age=604800"],"X-Frame-Options":["DENY"]}}
2021/06/28 04:09:53.519 DEBUG tls.issuance.acme.acme_client http request {"method": "POST", "url": "https://acme-v02.api.letsencrypt.org/acme/authz-v3/14352458491", "headers": {"Content-Type":["application/jose+json"],"User-Agent":["Caddy/2.3.0 CertMagic acmez (linux; amd64)"]}, "status_code": 200, "response_headers": {"Boulder-Requester":["118231829"],"Cache-Control":["public, max-age=0, no-cache"],"Content-Length":["384"],"Content-Type":["application/json"],"Date":["Mon, 28 Jun 2021 04:09:53 GMT"],"Link":["<https://acme-v02.api.letsencrypt.org/directory>;rel=\"index\""],"Replay-Nonce":["0003KJmcsve1jwNawhLghttcYSn6s86JuA0Wvdu_NpEirhk"],"Server":["nginx"],"Strict-Transport-Security":["max-age=604800"],"X-Frame-Options":["DENY"]}}
2021/06/28 04:09:53.520 DEBUG tls.issuance.acme.acme_client no solver configured {"challenge_type": "dns-01"}
2021/06/28 04:09:53.666 DEBUG tls.issuance.acme.acme_client http request {"method": "POST", "url": "https://acme-v02.api.letsencrypt.org/acme/authz-v3/14352458491", "headers": {"Content-Type":["application/jose+json"],"User-Agent":["Caddy/2.3.0 CertMagic acmez (linux; amd64)"]}, "status_code": 200, "response_headers": {"Boulder-Requester":["118231829"],"Cache-Control":["public, max-age=0, no-cache"],"Content-Length":["388"],"Content-Type":["application/json"],"Date":["Mon, 28 Jun 2021 04:09:53 GMT"],"Link":["<https://acme-v02.api.letsencrypt.org/directory>;rel=\"index\""],"Replay-Nonce":["0003sE6Sk6Bjq14Hy3ha895n-AypdpK3syTKFIpEKhfJ0Ao"],"Server":["nginx"],"Strict-Transport-Security":["max-age=604800"],"X-Frame-Options":["DENY"]}}
2021/06/28 04:09:53.667 INFO tls.issuance.acme waiting on internal rate limiter {"identifiers": ["*.example111.com"]}
2021/06/28 04:09:53.668 INFO tls.issuance.acme done waiting on internal rate limiter {"identifiers": ["*.example111.com"]}
2021/06/28 04:09:54.313 DEBUG tls.issuance.acme.acme_client http request {"method": "GET", "url": "https://acme.zerossl.com/v2/DV90", "headers": {"User-Agent":["Caddy/2.3.0 CertMagic acmez (linux; amd64)"]}, "status_code": 200, "response_headers": {"Access-Control-Allow-Origin":["*"],"Cache-Control":["max-age=-1"],"Content-Length":["645"],"Content-Type":["application/json"],"Date":["Mon, 28 Jun 2021 04:09:54 GMT"],"Server":["nginx"],"Strict-Transport-Security":["max-age=15552000"]}}
2021/06/28 04:09:55.061 DEBUG tls.issuance.acme.acme_client http request {"method": "HEAD", "url": "https://acme.zerossl.com/v2/DV90/newNonce", "headers": {"User-Agent":["Caddy/2.3.0 CertMagic acmez (linux; amd64)"]}, "status_code": 200, "response_headers": {"Access-Control-Allow-Origin":["*"],"Cache-Control":["max-age=-1"],"Content-Type":["application/octet-stream"],"Date":["Mon, 28 Jun 2021 04:09:55 GMT"],"Link":["<https://acme.zerossl.com/v2/DV90>;rel=\"index\""],"Replay-Nonce":["fBndGqG1__IV-MbxhDJqu5Y7gAd8CMtd32CMs_HdCH0"],"Server":["nginx"],"Strict-Transport-Security":["max-age=15552000"]}}
2021/06/28 04:09:56.123 DEBUG tls.issuance.acme.acme_client http request {"method": "POST", "url": "https://acme.zerossl.com/v2/DV90/newOrder", "headers": {"Content-Type":["application/jose+json"],"User-Agent":["Caddy/2.3.0 CertMagic acmez (linux; amd64)"]}, "status_code": 201, "response_headers": {"Access-Control-Allow-Origin":["*"],"Cache-Control":["max-age=0, no-cache, no-store","max-age=-1"],"Content-Length":["275"],"Content-Type":["application/json"],"Date":["Mon, 28 Jun 2021 04:09:56 GMT"],"Location":["https://acme.zerossl.com/v2/DV90/order/M7qer6yszLQB5ZeDNhLlaw"],"Replay-Nonce":["IlI_kFWZYrhfEwNfaF2eiD2sMbYyqMD6rKXGswKnWm4"],"Server":["nginx"],"Status":[""],"Strict-Transport-Security":["max-age=15552000"]}}
2021/06/28 04:09:56.823 DEBUG tls.issuance.acme.acme_client http request {"method": "POST", "url": "https://acme.zerossl.com/v2/DV90/authz/-I4D0eSwnTFCP0l1tuSYAA", "headers": {"Content-Type":["application/jose+json"],"User-Agent":["Caddy/2.3.0 CertMagic acmez (linux; amd64)"]}, "status_code": 200, "response_headers": {"Access-Control-Allow-Origin":["*"],"Cache-Control":["max-age=-1"],"Content-Length":["295"],"Content-Type":["application/json"],"Date":["Mon, 28 Jun 2021 04:09:56 GMT"],"Link":["<https://acme.zerossl.com/v2/DV90>;rel=\"index\""],"Replay-Nonce":["tT-N4s1_UMGdw6udyGrGTChqgbFlI0DGEFeuJBiz_7c"],"Retry-After":["5"],"Server":["nginx"],"Strict-Transport-Security":["max-age=15552000"]}}
2021/06/28 04:09:56.823 DEBUG tls.issuance.acme.acme_client no solver configured {"challenge_type": "dns-01"}
2021/06/28 04:09:57.328 DEBUG tls.issuance.acme.acme_client http request {"method": "POST", "url": "https://acme.zerossl.com/v2/DV90/authz/-I4D0eSwnTFCP0l1tuSYAA", "headers": {"Content-Type":["application/jose+json"],"User-Agent":["Caddy/2.3.0 CertMagic acmez (linux; amd64)"]}, "status_code": 200, "response_headers": {"Access-Control-Allow-Origin":["*"],"Cache-Control":["max-age=-1"],"Content-Length":["139"],"Content-Type":["application/json"],"Date":["Mon, 28 Jun 2021 04:09:57 GMT"],"Link":["<https://acme.zerossl.com/v2/DV90>;rel=\"index\""],"Replay-Nonce":["A_YgvXC1HnaSy99x4UtTBcJtC5DFmeY8Nqwkya1QA4Q"],"Retry-After":["5"],"Server":["nginx"],"Strict-Transport-Security":["max-age=15552000"]}}
2021/06/28 04:09:57.329 ERROR tls.obtain will retry {"error": "[*.example111.com] Obtain: [*.example111.com] solving challenges: *.example111.com: no solvers available for remaining challenges (configured=[http-01 tls-alpn-01] offered=[dns-01] remaining=[dns-01]) (order=https://acme.zerossl.com/v2/DV90/order/M7qer6yszLQB5ZeDNhLlaw) (ca=https://acme.zerossl.com/v2/DV90)", "attempt": 1, "retrying_in": 60, "elapsed": 4.876815429, "max_duration": 2592000}