Hello @matt
I got some news !
It was a bit different than usual, but I thinks it’s quite interesting.
Since last issue, I now monitor “no certificate available for *.lemlist.com” logs.
Yesterday (Sunday) at 15:54:36 (local time), I received an alert , but the alert quickly disappeared by itself. (compared to last time when issue stays until we restarted caddy)
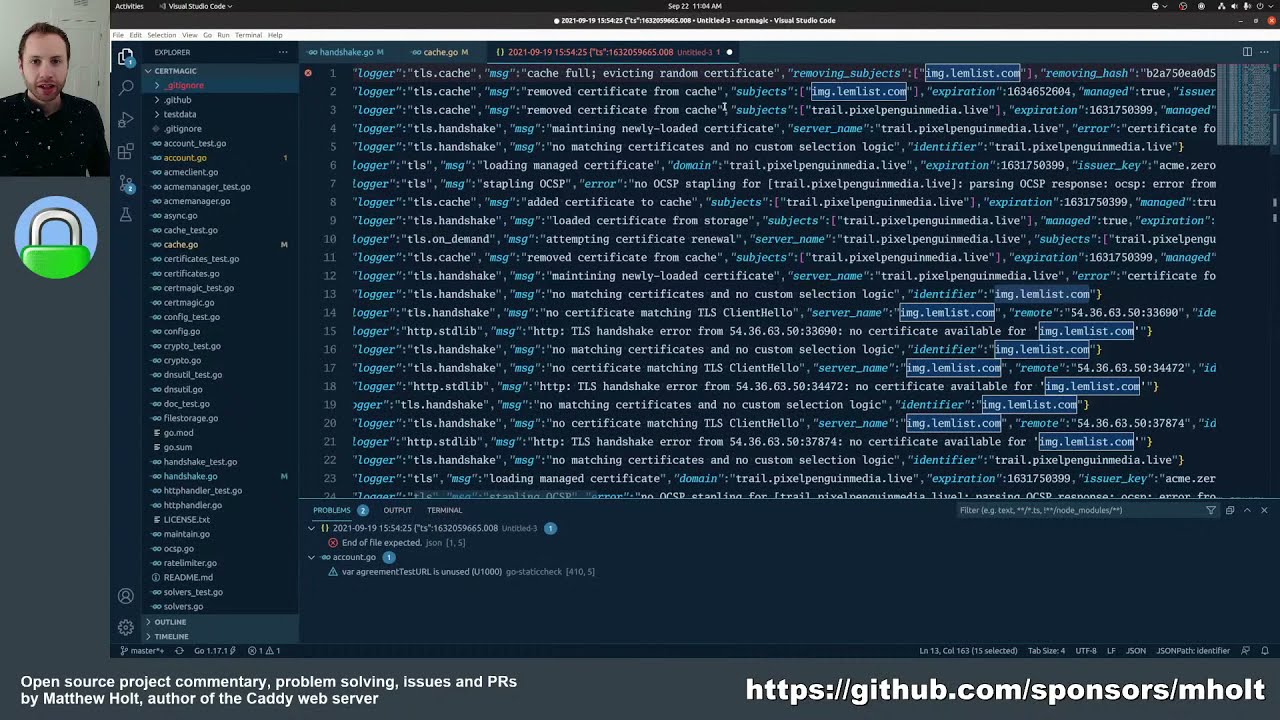
Here the logs when issue occurred:
logs | grep img.lemlist.com
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.0088575,"logger":"tls.cache","msg":"cache full; evicting random certificate","removing_subjects":["img.lemlist.com"],"removing_hash":"b2a750ea0d50222f9263392bf012c0d5f4cb06c7b1fea651358b8df21e48bbb1","inserting_subjects":["trail.pixelpenguinmedia.live"],"inserting_hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.0088665,"logger":"tls.cache","msg":"removed certificate from cache","subjects":["img.lemlist.com"],"expiration":1634652604,"managed":true,"issuer_key":"acme-v02.api.letsencrypt.org-directory","hash":"b2a750ea0d50222f9263392bf012c0d5f4cb06c7b1fea651358b8df21e48bbb1"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.8161275,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"img.lemlist.com"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.816262,"logger":"tls.handshake","msg":"no certificate matching TLS ClientHello","server_name":"img.lemlist.com","remote":"54.36.63.50:33690","identifier":"img.lemlist.com","cipher_suites":[4866,4867,4865,49199,49195,49200,49196,158,49191,103,49192,107,163,159,52393,52392,52394,49327,49325,49315,49311,49245,49249,49239,49235,162,49326,49324,49314,49310,49244,49248,49238,49234,49188,106,49187,64,49162,49172,57,56,49161,49171,51,50,157,49313,49309,49233,156,49312,49308,49232,61,60,53,47,255],"cache_size":9999,"cache_capacity":10000,"load_if_necessary":true,"obtain_if_necessary":true,"on_demand":false}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.816341,"logger":"http.stdlib","msg":"http: TLS handshake error from 54.36.63.50:33690: no certificate available for 'img.lemlist.com'"}
2021-09-19 15:54:27 {"level":"debug","ts":1632059667.6216931,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"img.lemlist.com"}
2021-09-19 15:54:27 {"level":"debug","ts":1632059667.6217434,"logger":"tls.handshake","msg":"no certificate matching TLS ClientHello","server_name":"img.lemlist.com","remote":"54.36.63.50:34472","identifier":"img.lemlist.com","cipher_suites":[4866,4867,4865,49199,49195,49200,49196,158,49191,103,49192,107,163,159,52393,52392,52394,49327,49325,49315,49311,49245,49249,49239,49235,162,49326,49324,49314,49310,49244,49248,49238,49234,49188,106,49187,64,49162,49172,57,56,49161,49171,51,50,157,49313,49309,49233,156,49312,49308,49232,61,60,53,47,255],"cache_size":9998,"cache_capacity":10000,"load_if_necessary":true,"obtain_if_necessary":true,"on_demand":false}
2021-09-19 15:54:27 {"level":"debug","ts":1632059667.6217873,"logger":"http.stdlib","msg":"http: TLS handshake error from 54.36.63.50:34472: no certificate available for 'img.lemlist.com'"}
2021-09-19 15:54:29 {"level":"debug","ts":1632059669.28179,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"img.lemlist.com"}
2021-09-19 15:54:29 {"level":"debug","ts":1632059669.2818348,"logger":"tls.handshake","msg":"no certificate matching TLS ClientHello","server_name":"img.lemlist.com","remote":"54.36.63.50:37874","identifier":"img.lemlist.com","cipher_suites":[4866,4867,4865,49199,49195,49200,49196,158,49191,103,49192,107,163,159,52393,52392,52394,49327,49325,49315,49311,49245,49249,49239,49235,162,49326,49324,49314,49310,49244,49248,49238,49234,49188,106,49187,64,49162,49172,57,56,49161,49171,51,50,157,49313,49309,49233,156,49312,49308,49232,61,60,53,47,255],"cache_size":9999,"cache_capacity":10000,"load_if_necessary":true,"obtain_if_necessary":true,"on_demand":false}
2021-09-19 15:54:29 {"level":"debug","ts":1632059669.281859,"logger":"http.stdlib","msg":"http: TLS handshake error from 54.36.63.50:37874: no certificate available for 'img.lemlist.com'"}
2021-09-19 15:54:31 {"level":"debug","ts":1632059671.1242878,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"img.lemlist.com"}
2021-09-19 15:54:31 {"level":"debug","ts":1632059671.1250055,"logger":"tls","msg":"loading managed certificate","domain":"img.lemlist.com","expiration":1634652604,"issuer_key":"acme-v02.api.letsencrypt.org-directory","storage":"FileStorage:/var/lib/caddy/.local/share/caddy"}
2021-09-19 15:54:31 {"level":"debug","ts":1632059671.2856934,"logger":"tls.cache","msg":"added certificate to cache","subjects":["img.lemlist.com"],"expiration":1634652604,"managed":true,"issuer_key":"acme-v02.api.letsencrypt.org-directory","hash":"b2a750ea0d50222f9263392bf012c0d5f4cb06c7b1fea651358b8df21e48bbb1"}
2021-09-19 15:54:31 {"level":"debug","ts":1632059671.2857137,"logger":"tls.handshake","msg":"loaded certificate from storage","subjects":["img.lemlist.com"],"managed":true,"expiration":1634652604,"hash":"b2a750ea0d50222f9263392bf012c0d5f4cb06c7b1fea651358b8df21e48bbb1"}
2
logs | grep trail.pixelpenguinmedia.live
2021-09-19 15:54:25 {"level":"debug","ts":1632059664.9676862,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"trail.pixelpenguinmedia.live"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059664.967935,"logger":"tls","msg":"loading managed certificate","domain":"trail.pixelpenguinmedia.live","expiration":1631750399,"issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/lib/caddy/.local/share/caddy"}
2021-09-19 15:54:25 {"level":"warn","ts":1632059665.0087621,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [trail.pixelpenguinmedia.live]: parsing OCSP response: ocsp: error from server: unauthorized"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.0088575,"logger":"tls.cache","msg":"cache full; evicting random certificate","removing_subjects":["img.lemlist.com"],"removing_hash":"b2a750ea0d50222f9263392bf012c0d5f4cb06c7b1fea651358b8df21e48bbb1","inserting_subjects":["trail.pixelpenguinmedia.live"],"inserting_hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.0088732,"logger":"tls.cache","msg":"added certificate to cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.008879,"logger":"tls.handshake","msg":"loaded certificate from storage","subjects":["trail.pixelpenguinmedia.live"],"managed":true,"expiration":1631750399,"hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:25 {"level":"info","ts":1632059665.0088873,"logger":"tls.on_demand","msg":"attempting certificate renewal","server_name":"trail.pixelpenguinmedia.live","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"remaining":-309266.008885306}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.0984578,"logger":"tls.cache","msg":"removed certificate from cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:25 {"level":"error","ts":1632059665.0984843,"logger":"tls.handshake","msg":"maintining newly-loaded certificate","server_name":"trail.pixelpenguinmedia.live","error":"certificate for hostname 'trail.pixelpenguinmedia.live' not allowed; non-2xx status code 404 returned from http://localhost:8000/api/cname/validate"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.222143,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"trail.pixelpenguinmedia.live"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.2223792,"logger":"tls","msg":"loading managed certificate","domain":"trail.pixelpenguinmedia.live","expiration":1631750399,"issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/lib/caddy/.local/share/caddy"}
2021-09-19 15:54:25 {"level":"warn","ts":1632059665.2635639,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [trail.pixelpenguinmedia.live]: parsing OCSP response: ocsp: error from server: unauthorized"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.2635863,"logger":"tls.cache","msg":"added certificate to cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.2635963,"logger":"tls.handshake","msg":"loaded certificate from storage","subjects":["trail.pixelpenguinmedia.live"],"managed":true,"expiration":1631750399,"hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:25 {"level":"info","ts":1632059665.2636049,"logger":"tls.on_demand","msg":"attempting certificate renewal","server_name":"trail.pixelpenguinmedia.live","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"remaining":-309266.263603222}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.3494341,"logger":"tls.cache","msg":"removed certificate from cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:25 {"level":"error","ts":1632059665.3494928,"logger":"tls.handshake","msg":"maintining newly-loaded certificate","server_name":"trail.pixelpenguinmedia.live","error":"certificate for hostname 'trail.pixelpenguinmedia.live' not allowed; non-2xx status code 404 returned from http://localhost:8000/api/cname/validate"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.4759164,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"trail.pixelpenguinmedia.live"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.476824,"logger":"tls","msg":"loading managed certificate","domain":"trail.pixelpenguinmedia.live","expiration":1631750399,"issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/lib/caddy/.local/share/caddy"}
2021-09-19 15:54:25 {"level":"warn","ts":1632059665.518483,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [trail.pixelpenguinmedia.live]: parsing OCSP response: ocsp: error from server: unauthorized"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.5185623,"logger":"tls.cache","msg":"added certificate to cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.5185988,"logger":"tls.handshake","msg":"loaded certificate from storage","subjects":["trail.pixelpenguinmedia.live"],"managed":true,"expiration":1631750399,"hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:25 {"level":"info","ts":1632059665.518637,"logger":"tls.on_demand","msg":"attempting certificate renewal","server_name":"trail.pixelpenguinmedia.live","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"remaining":-309266.518631825}
2021-09-19 15:54:25 {"level":"debug","ts":1632059665.6272013,"logger":"tls.cache","msg":"removed certificate from cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:25 {"level":"error","ts":1632059665.6272252,"logger":"tls.handshake","msg":"maintining newly-loaded certificate","server_name":"trail.pixelpenguinmedia.live","error":"certificate for hostname 'trail.pixelpenguinmedia.live' not allowed; non-2xx status code 404 returned from http://localhost:8000/api/cname/validate"}
2021-09-19 15:54:30 {"level":"debug","ts":1632059670.7709398,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"trail.pixelpenguinmedia.live"}
2021-09-19 15:54:30 {"level":"debug","ts":1632059670.7711987,"logger":"tls","msg":"loading managed certificate","domain":"trail.pixelpenguinmedia.live","expiration":1631750399,"issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/lib/caddy/.local/share/caddy"}
2021-09-19 15:54:30 {"level":"warn","ts":1632059670.8113856,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [trail.pixelpenguinmedia.live]: parsing OCSP response: ocsp: error from server: unauthorized"}
2021-09-19 15:54:30 {"level":"debug","ts":1632059670.8114069,"logger":"tls.cache","msg":"added certificate to cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:30 {"level":"debug","ts":1632059670.811415,"logger":"tls.handshake","msg":"loaded certificate from storage","subjects":["trail.pixelpenguinmedia.live"],"managed":true,"expiration":1631750399,"hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:30 {"level":"info","ts":1632059670.811425,"logger":"tls.on_demand","msg":"attempting certificate renewal","server_name":"trail.pixelpenguinmedia.live","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"remaining":-309271.811423246}
2021-09-19 15:54:31 {"level":"debug","ts":1632059670.9139826,"logger":"tls.cache","msg":"removed certificate from cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:31 {"level":"error","ts":1632059670.9140458,"logger":"tls.handshake","msg":"maintining newly-loaded certificate","server_name":"trail.pixelpenguinmedia.live","error":"certificate for hostname 'trail.pixelpenguinmedia.live' not allowed; non-2xx status code 404 returned from http://localhost:8000/api/cname/validate"}
2021-09-19 15:54:31 {"level":"debug","ts":1632059671.048918,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"trail.pixelpenguinmedia.live"}
2021-09-19 15:54:31 {"level":"debug","ts":1632059671.0491865,"logger":"tls","msg":"loading managed certificate","domain":"trail.pixelpenguinmedia.live","expiration":1631750399,"issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/lib/caddy/.local/share/caddy"}
2021-09-19 15:54:31 {"level":"warn","ts":1632059671.089311,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [trail.pixelpenguinmedia.live]: parsing OCSP response: ocsp: error from server: unauthorized"}
2021-09-19 15:54:31 {"level":"debug","ts":1632059671.0893378,"logger":"tls.cache","msg":"added certificate to cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:31 {"level":"debug","ts":1632059671.0893695,"logger":"tls.handshake","msg":"loaded certificate from storage","subjects":["trail.pixelpenguinmedia.live"],"managed":true,"expiration":1631750399,"hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:31 {"level":"info","ts":1632059671.0893848,"logger":"tls.on_demand","msg":"attempting certificate renewal","server_name":"trail.pixelpenguinmedia.live","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"remaining":-309272.089382587}
2021-09-19 15:54:31 {"level":"debug","ts":1632059671.2050972,"logger":"tls.cache","msg":"removed certificate from cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:31 {"level":"error","ts":1632059671.2051272,"logger":"tls.handshake","msg":"maintining newly-loaded certificate","server_name":"trail.pixelpenguinmedia.live","error":"certificate for hostname 'trail.pixelpenguinmedia.live' not allowed; non-2xx status code 404 returned from http://localhost:8000/api/cname/validate"}
2021-09-19 15:54:36 {"level":"debug","ts":1632059676.344953,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"trail.pixelpenguinmedia.live"}
2021-09-19 15:54:36 {"level":"debug","ts":1632059676.3452585,"logger":"tls","msg":"loading managed certificate","domain":"trail.pixelpenguinmedia.live","expiration":1631750399,"issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/lib/caddy/.local/share/caddy"}
2021-09-19 15:54:36 {"level":"warn","ts":1632059676.3887825,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [trail.pixelpenguinmedia.live]: parsing OCSP response: ocsp: error from server: unauthorized"}
2021-09-19 15:54:36 {"level":"debug","ts":1632059676.388804,"logger":"tls.cache","msg":"added certificate to cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:36 {"level":"debug","ts":1632059676.388815,"logger":"tls.handshake","msg":"loaded certificate from storage","subjects":["trail.pixelpenguinmedia.live"],"managed":true,"expiration":1631750399,"hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:36 {"level":"info","ts":1632059676.3888257,"logger":"tls.on_demand","msg":"attempting certificate renewal","server_name":"trail.pixelpenguinmedia.live","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"remaining":-309277.388824013}
2021-09-19 15:54:36 {"level":"debug","ts":1632059676.4603086,"logger":"tls.cache","msg":"removed certificate from cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:36 {"level":"error","ts":1632059676.460333,"logger":"tls.handshake","msg":"maintining newly-loaded certificate","server_name":"trail.pixelpenguinmedia.live","error":"certificate for hostname 'trail.pixelpenguinmedia.live' not allowed; non-2xx status code 404 returned from http://localhost:8000/api/cname/validate"}
2021-09-19 15:54:36 {"level":"debug","ts":1632059676.5932777,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"trail.pixelpenguinmedia.live"}
2021-09-19 15:54:36 {"level":"debug","ts":1632059676.5934837,"logger":"tls","msg":"loading managed certificate","domain":"trail.pixelpenguinmedia.live","expiration":1631750399,"issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/lib/caddy/.local/share/caddy"}
2021-09-19 15:54:36 {"level":"warn","ts":1632059676.6338751,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [trail.pixelpenguinmedia.live]: parsing OCSP response: ocsp: error from server: unauthorized"}
2021-09-19 15:54:36 {"level":"debug","ts":1632059676.6339047,"logger":"tls.cache","msg":"added certificate to cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:36 {"level":"debug","ts":1632059676.6339223,"logger":"tls.handshake","msg":"loaded certificate from storage","subjects":["trail.pixelpenguinmedia.live"],"managed":true,"expiration":1631750399,"hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:36 {"level":"info","ts":1632059676.6339362,"logger":"tls.on_demand","msg":"attempting certificate renewal","server_name":"trail.pixelpenguinmedia.live","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"remaining":-309277.633934441}
2021-09-19 15:54:36 {"level":"debug","ts":1632059676.7237735,"logger":"tls.cache","msg":"removed certificate from cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:36 {"level":"error","ts":1632059676.7237947,"logger":"tls.handshake","msg":"maintining newly-loaded certificate","server_name":"trail.pixelpenguinmedia.live","error":"certificate for hostname 'trail.pixelpenguinmedia.live' not allowed; non-2xx status code 404 returned from http://localhost:8000/api/cname/validate"}
2021-09-19 15:54:36 {"level":"debug","ts":1632059676.8481839,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"trail.pixelpenguinmedia.live"}
2021-09-19 15:54:36 {"level":"debug","ts":1632059676.8484006,"logger":"tls","msg":"loading managed certificate","domain":"trail.pixelpenguinmedia.live","expiration":1631750399,"issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/lib/caddy/.local/share/caddy"}
2021-09-19 15:54:37 {"level":"warn","ts":1632059676.8900928,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [trail.pixelpenguinmedia.live]: parsing OCSP response: ocsp: error from server: unauthorized"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059676.8901165,"logger":"tls.cache","msg":"added certificate to cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059676.8901267,"logger":"tls.handshake","msg":"loaded certificate from storage","subjects":["trail.pixelpenguinmedia.live"],"managed":true,"expiration":1631750399,"hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:37 {"level":"info","ts":1632059676.8901362,"logger":"tls.on_demand","msg":"attempting certificate renewal","server_name":"trail.pixelpenguinmedia.live","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"remaining":-309277.890134641}
2021-09-19 15:54:37 {"level":"debug","ts":1632059676.9931116,"logger":"tls.cache","msg":"removed certificate from cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:37 {"level":"error","ts":1632059676.9931266,"logger":"tls.handshake","msg":"maintining newly-loaded certificate","server_name":"trail.pixelpenguinmedia.live","error":"certificate for hostname 'trail.pixelpenguinmedia.live' not allowed; non-2xx status code 404 returned from http://localhost:8000/api/cname/validate"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.1291041,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"trail.pixelpenguinmedia.live"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.1293235,"logger":"tls","msg":"loading managed certificate","domain":"trail.pixelpenguinmedia.live","expiration":1631750399,"issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/lib/caddy/.local/share/caddy"}
2021-09-19 15:54:37 {"level":"warn","ts":1632059677.1711495,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [trail.pixelpenguinmedia.live]: parsing OCSP response: ocsp: error from server: unauthorized"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.1712227,"logger":"tls.cache","msg":"added certificate to cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.171264,"logger":"tls.handshake","msg":"loaded certificate from storage","subjects":["trail.pixelpenguinmedia.live"],"managed":true,"expiration":1631750399,"hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:37 {"level":"info","ts":1632059677.1712997,"logger":"tls.on_demand","msg":"attempting certificate renewal","server_name":"trail.pixelpenguinmedia.live","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"remaining":-309278.171294399}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.331669,"logger":"tls.cache","msg":"removed certificate from cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:37 {"level":"error","ts":1632059677.3317065,"logger":"tls.handshake","msg":"maintining newly-loaded certificate","server_name":"trail.pixelpenguinmedia.live","error":"certificate for hostname 'trail.pixelpenguinmedia.live' not allowed; non-2xx status code 404 returned from http://localhost:8000/api/cname/validate"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.4557936,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"trail.pixelpenguinmedia.live"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.4561303,"logger":"tls","msg":"loading managed certificate","domain":"trail.pixelpenguinmedia.live","expiration":1631750399,"issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/lib/caddy/.local/share/caddy"}
2021-09-19 15:54:37 {"level":"warn","ts":1632059677.5002418,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [trail.pixelpenguinmedia.live]: parsing OCSP response: ocsp: error from server: unauthorized"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.5002878,"logger":"tls.cache","msg":"added certificate to cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.5003138,"logger":"tls.handshake","msg":"loaded certificate from storage","subjects":["trail.pixelpenguinmedia.live"],"managed":true,"expiration":1631750399,"hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:37 {"level":"info","ts":1632059677.5003366,"logger":"tls.on_demand","msg":"attempting certificate renewal","server_name":"trail.pixelpenguinmedia.live","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"remaining":-309278.500333675}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.5923948,"logger":"tls.cache","msg":"removed certificate from cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:37 {"level":"error","ts":1632059677.5924244,"logger":"tls.handshake","msg":"maintining newly-loaded certificate","server_name":"trail.pixelpenguinmedia.live","error":"certificate for hostname 'trail.pixelpenguinmedia.live' not allowed; non-2xx status code 404 returned from http://localhost:8000/api/cname/validate"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.7198083,"logger":"tls.handshake","msg":"no matching certificates and no custom selection logic","identifier":"trail.pixelpenguinmedia.live"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.720025,"logger":"tls","msg":"loading managed certificate","domain":"trail.pixelpenguinmedia.live","expiration":1631750399,"issuer_key":"acme.zerossl.com-v2-DV90","storage":"FileStorage:/var/lib/caddy/.local/share/caddy"}
2021-09-19 15:54:37 {"level":"warn","ts":1632059677.7681725,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [trail.pixelpenguinmedia.live]: parsing OCSP response: ocsp: error from server: unauthorized"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.7682037,"logger":"tls.cache","msg":"added certificate to cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.7682135,"logger":"tls.handshake","msg":"loaded certificate from storage","subjects":["trail.pixelpenguinmedia.live"],"managed":true,"expiration":1631750399,"hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:37 {"level":"info","ts":1632059677.7682214,"logger":"tls.on_demand","msg":"attempting certificate renewal","server_name":"trail.pixelpenguinmedia.live","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"remaining":-309278.768220023}
2021-09-19 15:54:37 {"level":"debug","ts":1632059677.8403103,"logger":"tls.cache","msg":"removed certificate from cache","subjects":["trail.pixelpenguinmedia.live"],"expiration":1631750399,"managed":true,"issuer_key":"acme.zerossl.com-v2-DV90","hash":"debd059c9153d172ff0dc0b110d4b2adb62ed065af002601da25f0a8c285c1a6"}
2021-09-19 15:54:37 {"level":"error","ts":1632059677.8403325,"logger":"tls.handshake","msg":"maintining newly-loaded certificate","server_name":"trail.pixelpenguinmedia.live","error":"certificate for hostname 'trail.pixelpenguinmedia.live' not allowed; non-2xx status code 404 returned from http://localhost:8000/api/cname/validate"}