1. Caddy version (caddy version):
[developer@code-server-fs bin]$ /opt/bin/caddy version
v2.2.1 h1:Q62GWHMtztnvyRU+KPOpw6fNfeCD3SkwH7SfT1Tgt2c=
[developer@code-server-fs bin]$ /opt/bin/caddy list-modules
admin.api.load
admin.api.metrics
caddy.adapters.caddyfile
caddy.listeners.tls
caddy.logging.encoders.console
caddy.logging.encoders.filter
caddy.logging.encoders.filter.delete
caddy.logging.encoders.filter.ip_mask
caddy.logging.encoders.json
caddy.logging.encoders.logfmt
caddy.logging.encoders.single_field
caddy.logging.writers.discard
caddy.logging.writers.file
caddy.logging.writers.net
caddy.logging.writers.stderr
caddy.logging.writers.stdout
caddy.storage.file_system
dns.providers.cloudflare
http
http.authentication.hashes.bcrypt
http.authentication.hashes.scrypt
http.authentication.providers.http_basic
http.encoders.gzip
http.encoders.zstd
http.handlers.acme_server
http.handlers.authentication
http.handlers.encode
http.handlers.error
http.handlers.file_server
http.handlers.headers
http.handlers.map
http.handlers.metrics
http.handlers.push
http.handlers.request_body
http.handlers.reverse_proxy
http.handlers.rewrite
http.handlers.static_response
http.handlers.subroute
http.handlers.templates
http.handlers.vars
http.matchers.expression
http.matchers.file
http.matchers.header
http.matchers.header_regexp
http.matchers.host
http.matchers.method
http.matchers.not
http.matchers.path
http.matchers.path_regexp
http.matchers.protocol
http.matchers.query
http.matchers.remote_ip
http.matchers.vars
http.matchers.vars_regexp
http.reverse_proxy.selection_policies.first
http.reverse_proxy.selection_policies.header
http.reverse_proxy.selection_policies.ip_hash
http.reverse_proxy.selection_policies.least_conn
http.reverse_proxy.selection_policies.random
http.reverse_proxy.selection_policies.random_choose
http.reverse_proxy.selection_policies.round_robin
http.reverse_proxy.selection_policies.uri_hash
http.reverse_proxy.transport.fastcgi
http.reverse_proxy.transport.http
pki
tls
tls.certificates.automate
tls.certificates.load_files
tls.certificates.load_folders
tls.certificates.load_pem
tls.handshake_match.sni
tls.issuance.acme
tls.issuance.internal
tls.issuance.zerossl
tls.stek.distributed
tls.stek.standard
2. How I run Caddy:
Docker, with custom executable file aquired from the download page with tls.dns.cloudflare plugin
a. System environment:
Docker
b. Command:
paste command here
d. My complete Caddyfile or JSON config:
http://project.tld, http://www.project.tld {
root * /home/project/www
templates
file_server {
index index.html
}
}
ssl.project.tld {
root * /home/project/www
templates
file_server {
index index.html
}
tls {
dns cloudflare APIKEY(Edit zone DNS Zone.DNS)
}
}
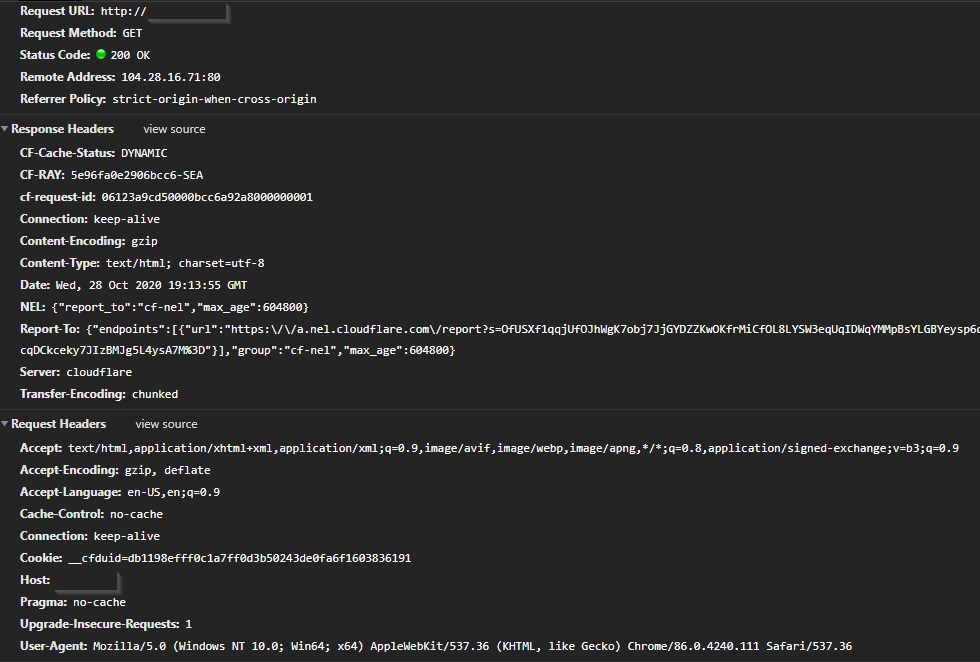
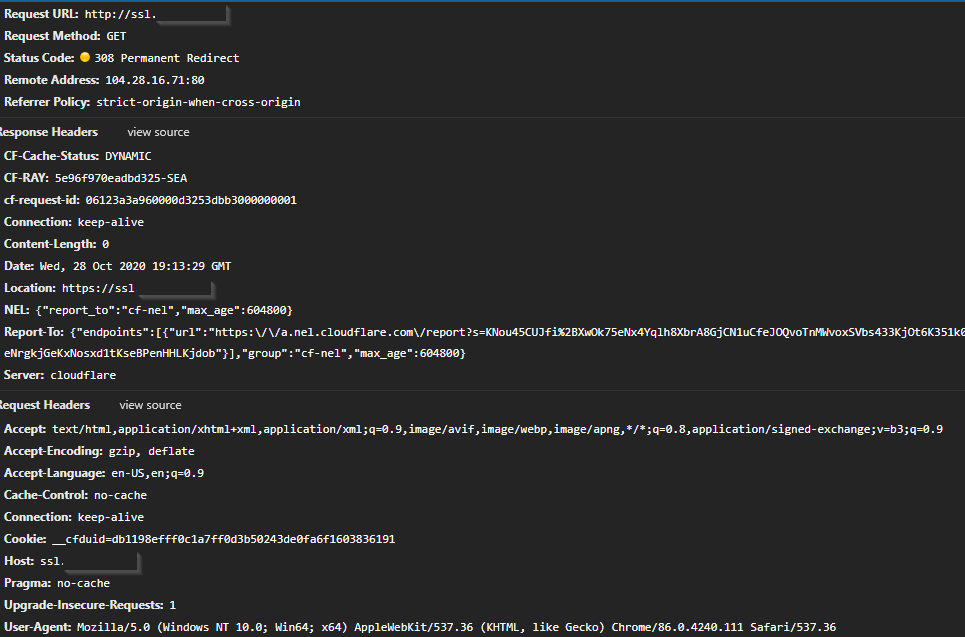
3. The problem I’m having:
No matter what i do, when i use Cloudflare Proxy, i get stuck in a redirect loop because of cloudflare requesting the http content to proxy, but caddy gives it a 301 redirect to https so all the user sees when they visit, is that 301 redirect, which keeps looping
Basically i need to disable the auto upgrade function, but i use caddyfiles, not json configs, which DONT have that feature as far as i can find in the damned docs
4. Error messages and/or full log output:
ERR_TOO_MANY_REDIRECTS in chrome
5. What I already tried:
I have no clue what to try, litterally no bloody clue.
The only thing that fixes it is one of two
- use full End2End Encryption with cloudflare (not an option due to the nature of the project i am wokring on)
- Dont use cloudflare proxy (again, not an option as i self host my crap and need cloudflare’s cache to not kill my home network when someone accesses my webserver