Hello, I am trying to get local HTTPS on my VPN. I created a simplified version of my caddyfile
bitwarden.private {
respond hello
]
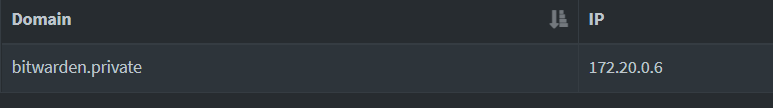
Within Pi-Hole I configured the domain to point to the ip address of the docker container like so:
But I am not getting a hello response it just goes to the docker container with no https.